what is Trojan:VBS/Crypter.A?
Trojan:VBS/Crypter.A is classified as the Trojan horse which is aimed to collect and steal your confidential information. Usually it spread itself via spam email attachments or other computer threats like Trojans, worms, rogue programs, etc. therefore, we should be careful before we open the email or download freeware online. Many computer users have tried to remove it on their own but they found it is hard to figure out the related files of the Trojan:VBS/Crypter.A for it can use and drops other random files names to disguise its related files.
What harms can it bring to your computer? To live with this Trojan:VBS/Crypter.A, it can automatically run every time you launch your computer for it add the registry to the startup items. After it gets itself installed, it can modify your default system settings and my operate on your computer backdoor to invite other similar infections to come into your computer. Beside, sine it will occupy the big part of your system resource, your computer may encounter system crash or computer freezing or it will block you accessing legit programs. have tried various ways but still cannot get rid of it on your own? You are welcome to follow the removal guide listed below:
Solution one: Get rid of Trojan:VBS/Crypter.A by automatic scan of SpyHunter removal tool
SpyHunter is a powerful, real-time anti-spyware application that designed to help computer users to clean up the infections like worms, Trojans, rootkits, rogues, dialers, spyware,etc. It is important to note that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step one: Click the icon to download SpyHunter removal tool
Follow the instructions to install SpyHunter removal tool
Step two: After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your PC
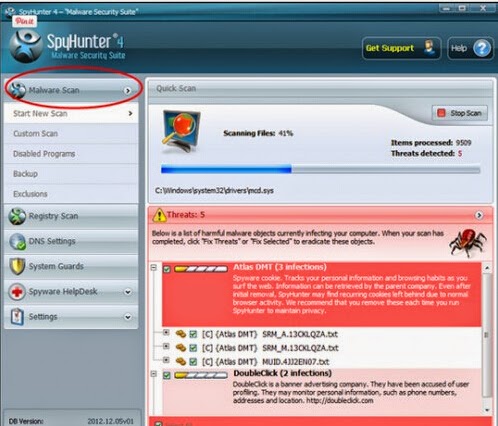
Step three: Select the detected malicious files after your scanning and click “Remove” button to clean up all viruses.

No comments:
Post a Comment