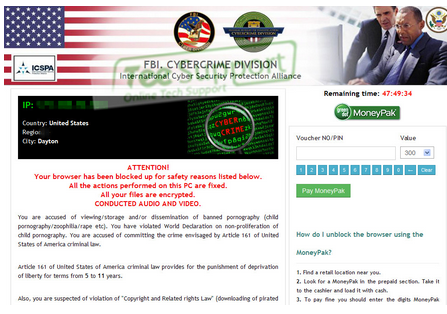
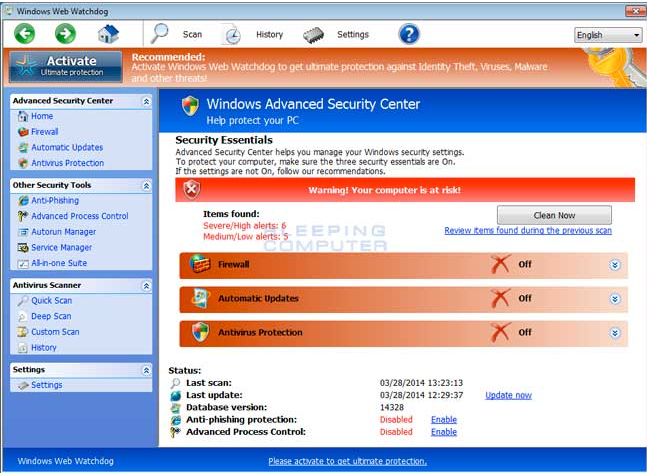
Basic Information on Trojan Horse PSW.Generic11.CIZG
Do you know more about Trojan Horse PSW.Generic11.CIZG? Trojan Horse PSW.Generic11.CIZG is classified as the Trojan horse infection which is firstly reported by AVG and classified it as a high risk threat. How come it gets into your computer without your knowledge? Firstly, it can get itself bundle with the free software downloads or embed its malicious codes onto the spam email attachments, therefore, you may be infected by this malicious virus via downloading free software without paying attention to the default installation of the free software or visiting questionable websites frequently. after it get itself installed on your computer, it can add the registry to the startup items to make itself automatically run every time you launch your computer. Thus, it would be better to keep your antivirus up to date to avoid the virus attack.
What can Trojan Horse PSW.Generic11.CIZG do on your computer?
- It can alter your default system settings and bypass the antivirus to get into your computer.
- Unexplained system crash or blue screen.
- It can operate on your computer backdoor to monitor your online traces or even steal your personal information, which will violate your privacy and put your personal information in danger.
- It can take up your system resource and then degrade your overall computer performance.
- It will make your system vulnerable for other malware.