More about "<random character>.xtbl"
"<random character>.xtbl" is caused by virus that comes into your computer via share files, spam email attachments, or infected software. Once infected, this encrypted virus will affect files that stored on your local C drive and E drive. There will be a readme.txt file left in your local drive and ask you to send 0FA1C3DC72226AF540AC|0 code to e-mail address decode0098@gmail.com or decode00987@gmail.com. And then you can receive details instructions to decrypt your files. Please don’t be cheated. You should remove the encrypted virus as soon as possible because it will not only encrypt your files but steal your important data like user names and passwords for different accounts stored on your computer.
Remove "<random character>.xtbl" Encrypted Virus and Decrypt Files
Here are some feasible solutions that can help you remove the encrypted virus and decrypt all the infected files.
Suggestion 1:Watch Removal Video for Reference
Suggestion 2: Remove Encrypted Virus and Decrypt Files with SpyHunter
SpyHunter has the ability to detect and remove rootkits, which are used to stealth install rogue anti-spyware programs and other trojans. It is designed to assist the average computer user in protecting their PC from malicious threats. You can remove the existence viruses in your computer and decryt your files encypted by "<random character>.xtbl"


SpyHunter's free scanner is for malware detection. You have the choice of buying SpyHunter for malware removal. Here are some install procedures for it. You can read it for reference.
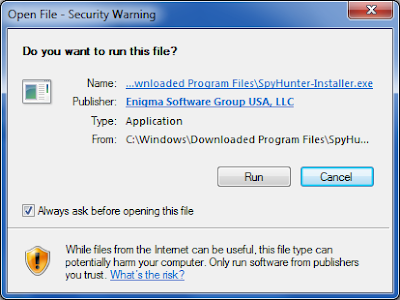
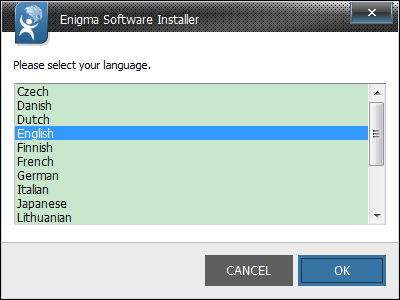
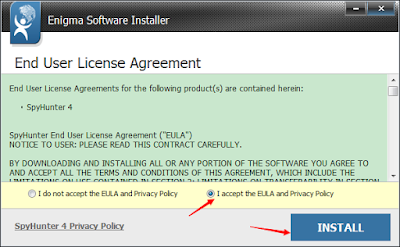
Step 1: After finishing downloading, click Run to install SpyHunter step by step.
...
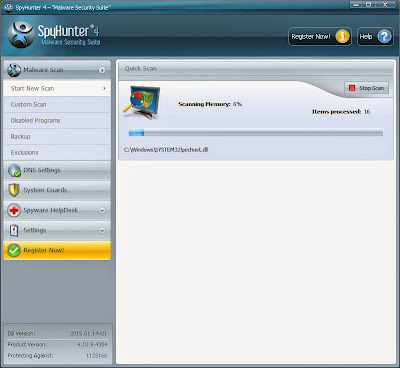
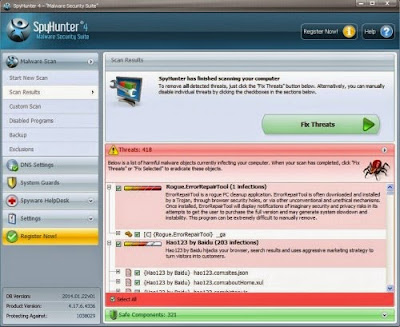
Step 2: After finishing installing, SpyHunter will scan and diagnose your entire system automatically.
Step 3: As the scanning is complete, all detected threats will be listed out. Then, you can click on “Fix Threats” to remove all of the threats found in your system.
Good to know:
SpyHunter responds with advanced technology to stay one step ahead of today’s malware threats. It offers additional customization capabilities to ensure every user is able to custom tailor this anti-malware application to fit their specific needs. It is great if you remove the threats on your own. If you cannot make it yourself, SpyHunter will be another choice for you.
No comments:
Post a Comment